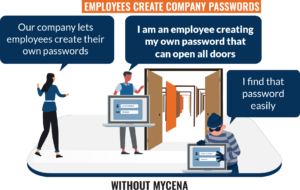
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
IAM, PAM, SSO, password managers |
MyCena® Encrypted Access Management |
|
|---|---|---|
Knowledge of Passwords |
Yes
|
No
|
Password Strength |
Weak
|
Strong
|
Risk Of Password Theft |
High
|
Low
|
Access Segmentation |
No
|
Yes
|
Access Layers |
No
|
Yes
|
Password Resets |
Yes
|
No
|
Access Flexibility |
No
|
Yes
|
Governance |
No
|
Yes
|
Risk Of Lateral Movement, Privilege Escalation, Ransomware, Supply-chain Attacks |
High
|
Low
|
Password Expiry |
No
|
Yes
|
Blocks Save Passwords In Browser And Windows Clipboard |
No |
Yes |
One-click Access ( Automatic Transport Of Passwords Without Typing Or Seing Password) |
No |
Yes |
Integration With Infrastructure Protocols (Telnet, SSH, RDP, Etc.), Websites (Http/Https), Local And Legacy Applications |
No |
Yes |
Integration Of GRC Module With Syslog Solutions (SIEM, Splunk) |
No |
Yes |
Centralized Credentials Management |
No |
Yes |
Credit Card Module |
No |
Yes |