By MyCena | Posted on: 4 June 2025
IAM vs. PAM: Why Understanding the Difference is Key to Your Cybersecurity Strategy
In today's digital landscape, managing access isn't just an IT task—it's a critical line of defense. Two
terms often thrown around in the cybersecurity world are IAM (Identity Access Management) and PAM
(Privileged Access Management) . They sound similar, and they are related—but mixing them up could
leave your systems exposed in ways you didn't expect.
Let's break them down and explain how each plays a unique (and essential) role in keeping your
organization secure.
What is IAM?
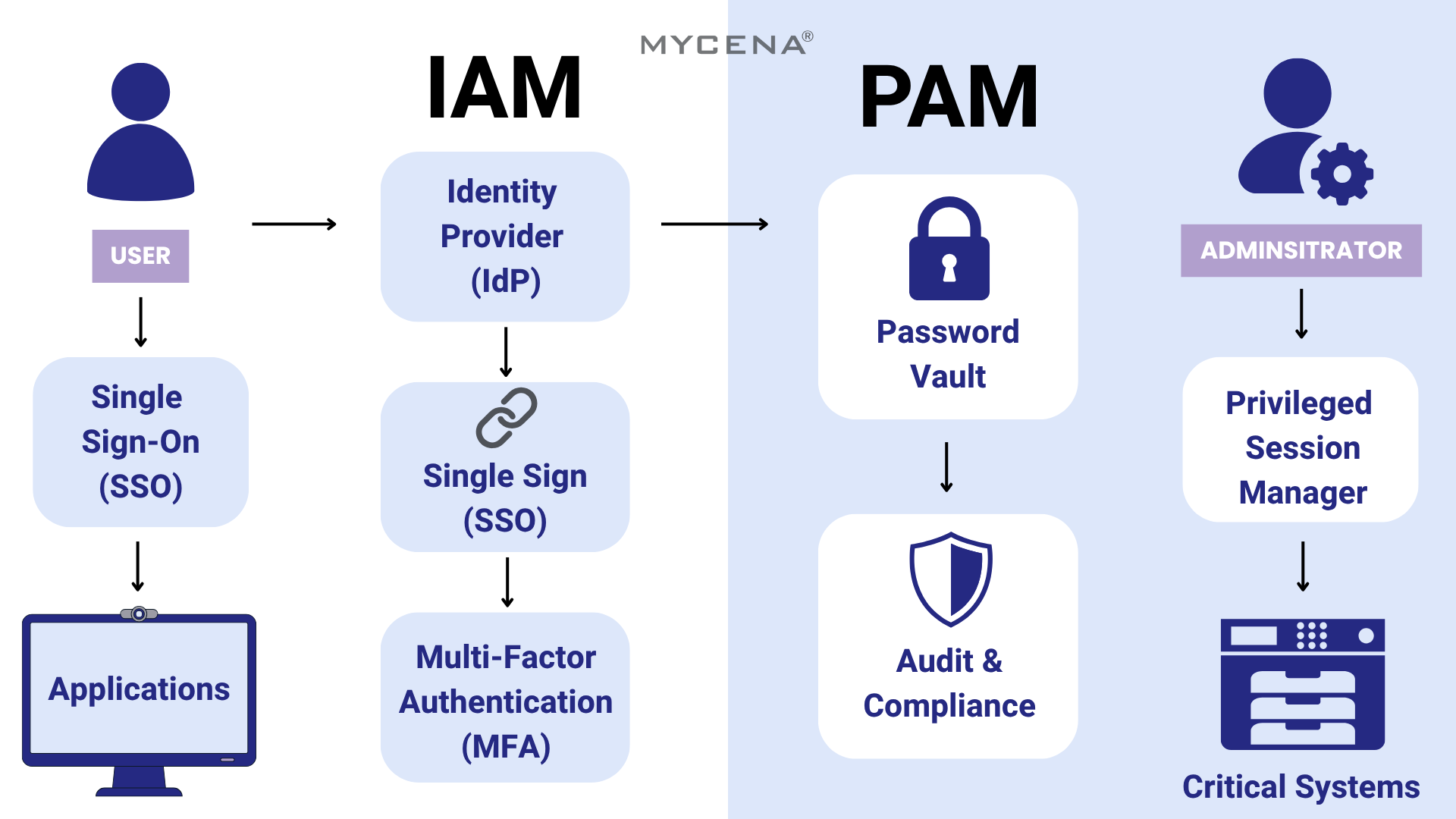
Identity and Access Management (IAM) is the foundational layer of digital access
control. It's like the
front desk of
your digital office—checking who each person is and what they're allowed to do.
IAM ensures that every user , whether it's an employee, customer, contractor, or
partner, has the right
level of
access to the right resources —nothing more, nothing less.
IAM systems handle:
- Creating and managing user identities across systems
- Controlling logins with secure methods like Single Sign-On (SSO), multi-factor authentication (MFA), or
biometrics
- Automating onboarding and offboarding processes
- Assigning access based on roles (RBAC)
- Tracking who accessed what and when (audit trails)
Popular IAM tools: Okta, Microsoft Entra ID (formerly Azure AD), Auth0
Think of IAM as the digital ID badge and access gate for everyone in your ecosystem.
What is PAM?
While IAM is about everyone , Privileged Access Management (PAM) is about the few — the
users who hold
the digital master keys.
PAM is a specialized subset of IAM focused on securing privileged accounts , such as
system
administrators, DevOps engineers, and IT staff. These accounts can access your most critical infrastructure, and if
compromised, they can cause catastrophic damage.
PAM solutions are designed to:
- Store and manage powerful credentials in secure password vaults
- Monitor and record sessions of users with elevated privileges
- Enforce Just-In-Time (JIT) access (temporary, on-demand permissions)
- Detect unusual or risky behavior through user behavior analytics
- Enforce Segregation of Duties (SoD) to prevent conflicts of interest
Popular PAM tools: CyberArk, BeyondTrust, Delinea (formerly Thycotic)
Where IAM manages the front door for everyone, PAM secures the keys to the server room.
IAM vs. PAM: Quick Comparison
| Feature |
IAM |
PAM |
| Who it covers |
All users (staff, partners, customers) |
Privileged users (admins, IT, DevOps) |
| Main goal |
Manage user identities and general access |
Protect and monitor high-risk access |
| Focus |
Authentication & role-based access |
Secure credential vaulting & session control |
| Use case |
Needed by all organizations |
Critical for sensitive or regulated systems |
Why You Need Both
Relying on IAM without PAM is like having a well-guarded office lobby but no lock on the server room.
Conversely, using PAM without IAM would be like locking up the IT admin while leaving the rest of the building open.
For a robust access security strategy, you need both IAM and PAM working together :
- IAM ensures everyone is verified and appropriately authorized.
- PAM ensures only the right people , at the right time, can touch your most sensitive systems—with oversight and
control.
Final Thoughts
As cyber threats grow more advanced—especially with phishing, insider risks, and AI-driven
attacks—relying solely on traditional identity or access tools leaves gaps. IAM and PAM are
essential pieces of the
security puzzle, but they still depend on one vulnerable element: human-managed credentials.
That's where MyCena® comes in.
MyCena® takes IAM and PAM a step further by removing the weakest link in the chain,
passwords. With
encrypted, automated credential management, MyCena® ensures employees never create, see, or share
credentials. That
makes phishing irrelevant, access segmented, and compliance a breeze.
By complementing your IAM and PAM strategies, MyCena® helps eliminate credential-based
attacks entirely
, simplifying governance while boosting your organization's resilience and efficiency.
No passwords. No phishing. No problem.
MyCena®. Security done for you.